- Web firewalls with many unnecessary events can allow false detection that blocks normal traffic and WAF-blocked attacks.
- Imperva's research center ensures the accuracy of detection of client web firewalls in response to changes in the web security threat environment
SecureSphere
Imperva Web Firewall
Imperva Web Firewall defends OWASP TOP10 as well as advanced threatened applications with the latest technology.
 SQL Injection
SQL Injection XSS
XSS SSL
SSL Block upload
Block upload Brute force
Brute force Session hijacking / Cookie modulation
Session hijacking / Cookie modulation
/ Parameter modulation Applicaiton
Applicaiton
Intelligence Sensitive information leakage
Sensitive information leakage Bot Cut-off
Bot Cut-off CSRF
CSRF
Automation /
Application
Attack Defense Correlation analysis
Correlation analysis Virtual Patching
Virtual Patching Custom Policies
Custom Policies Positive Security
Positive Security
Basics of Web Firewall
Reliability and Security
Noise-free Web Firewall Operations
Operating in 100% blocking mode for domestic customers
Reduce Web Application Risk
- Automated policy creation and regular signature updates twice a month enable you to quickly and securely secure web application security at the speed of your DevOPs team.
Provides the world's best signature DB and update services
Provide an optimized configuration environment
for your network and production environment
Based on the deployment experience and know-how of On-Prem, Public/Private Cloud, we provide deployment services optimized for customer requirements/network environments.
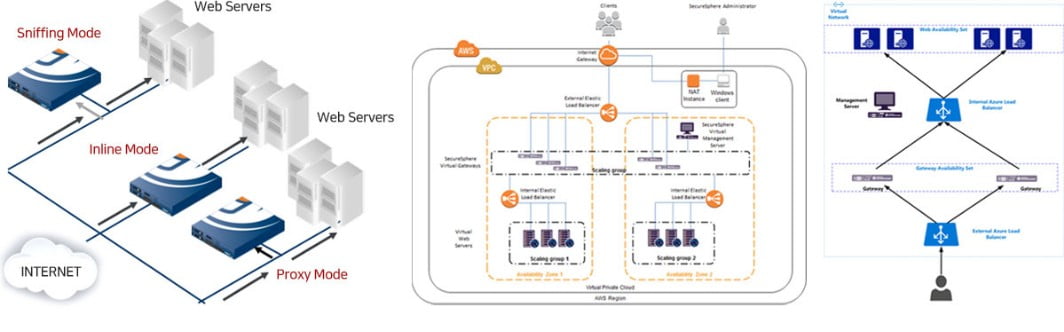
Supported Platform
-
 On-Prem
On-Prem
-


 Public Cloud
Public Cloud
-


 Private Cloud
Private Cloud
- Trusted manufacturers with cloud operators and security parknership
- Technical support from experienced cloud-specialized web firewall engineers
- Have multiple deployment references
Automated response to security threats
-
 Exactly
Exactly
Who
accessed what data? -
 Is this behavior
Is this behavior
Normal Access?
-
 How do I know and
How do I know and
How Quickly
can I respond?
And if not?
The core of DB security threats is an automated business process.
-
Navigation, Classification, Evaluation Search for sensitive information, check for vulnerabilities
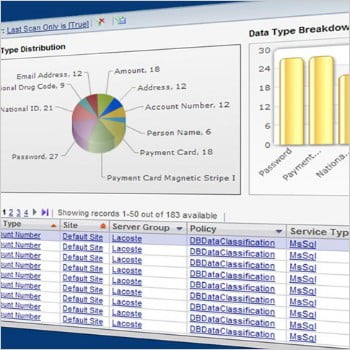 Key FeaturesPlatform-agnostic navigation
Key FeaturesPlatform-agnostic navigation- On-Prem
- Private/Public Cloud
Unauthorized DB server detection- Automatic detection of unidentified DB servers by security team
Unauthorized DB server detection- Flexible Tam using built-in signatures and regular expressions
- Over 1,500 DISAs (STIGs), CIS benchmark vulnerabilities testing, known DB server vulnerabilities detection, and security patch detection support
-
Data Activity Monitoring/Blocking Detect/alarm/block continuous database access behavior
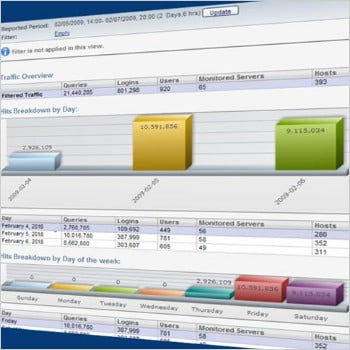 Key FeaturesProvides visibility into who accessed what
Key FeaturesProvides visibility into who accessed what
data, including authorized users- A predefined audit policy related to the Privacy Act
- Customized security policies with custom policies
Provides a standardized DB security audit framework for various platforms(On-Prem/Private, Public Cloud)- Simplify DB Security Audit
- Easy DB audit expansion in hybrid environments
Identify whether sensitive information is present and should be regulated -
Database Security Configuration Detect/alarm/block continuous database access behavior
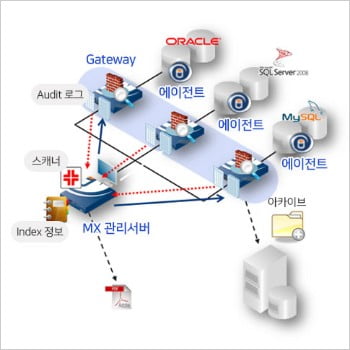 Gateway
Gateway- Devices that monitor and control traffic to the DB server
- Save real-time audit logs
MX Management Server- GW Integrated management (Security Policy, Audit Integrated management)
- DB Activity Monitoring and gathering index information
- Provide DB Scanner
Agent- Agent applications that you install on the DB server
- Monitor and block all operations over the network
or after connecting directly to the DB
Supported Database
Security personnel's concerns
-
27%
Customers face millions of
security events per day -
83%
Loaded with multiple
security solutions -
83%
a series of false detections
-
4 Hours
Minimum business hours for
daily Alert analysis
Attack Analysis Architecture
Reporting key web security issues through on-prem, public/private cloud impact management server (MX)
security events collection/analysis machine learning/AI/crowsing-based insights
security events collection/analysis machine learning/AI/crowsing-based insights

Gain insight with Attack Analysis
Automatically categorizes key incidents in millions of events based on machine learning/AI/crowd sourcing,
and security personnel can immediately take action on key incidents without any analysis
and security personnel can immediately take action on key incidents without any analysis


“ Increasing Visibility into threats
Make Decisions based on threat information
Protect your core information in your enterprise ”
Make Decisions based on threat information
Protect your core information in your enterprise ”

Easy transition to SECaaS
- Simple and fast transition to an Impoverbar Cloud DDoS-enabled solution with DNS server changes
- Seoul Region POP construction provides WEB DDos/WAF (SECaaS) services without delay
- Block automated Web DDoS attacks without operator intervention
- 47 dedicated global data centers
- Accept up to 6TB of traffic
- Fast propagation/security updates to self-developed systems
- Global network 95% latency of 50ms or less
- Handles traffic close to 47 global POPs
- SDN Transitions Fast Routing with Tier 1 ISP Integration
- Accurate detection capabilities: single stack (L3 to L7 protection), deep inspection and protection,
eputation intelligence for impingement threats, unlimited defense regardless of attack volume - Fast speed and blocking : Domestic POP, SLA to respond within 3 seconds, SD-NOC/SOC (99.999% SLA),
Advanced Edge Routing, Global Mesh Configuration


High Visibility
- DDoS attacks used as camouflage tactics allow for detailed visibility of actual end goals and attacks during defense
| Accurate detection | Fast speed and blocking | High visibility |
|---|---|---|
|
|
|
Global Leader Group
Founded in 2002, Infar is a security company that supplies web security/DB security solutions to more than 5,900 customers
worldwide. Gartner has selected him as the only global leader in the web firewall market for seven consecutive years between 2014 and 2020.
worldwide. Gartner has selected him as the only global leader in the web firewall market for seven consecutive years between 2014 and 2020.
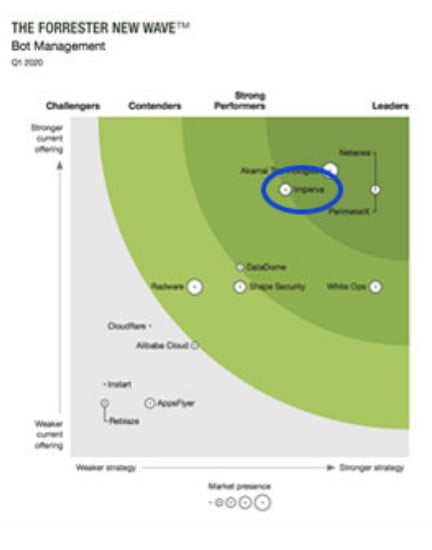 bot
bot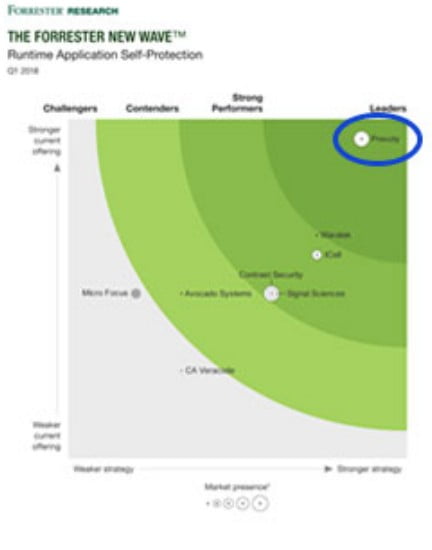 rasp
rasp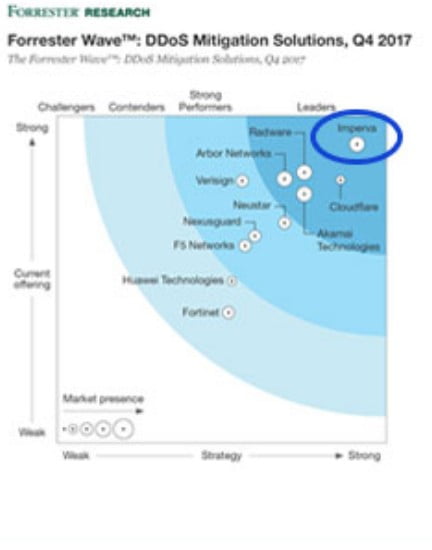 ddos
ddos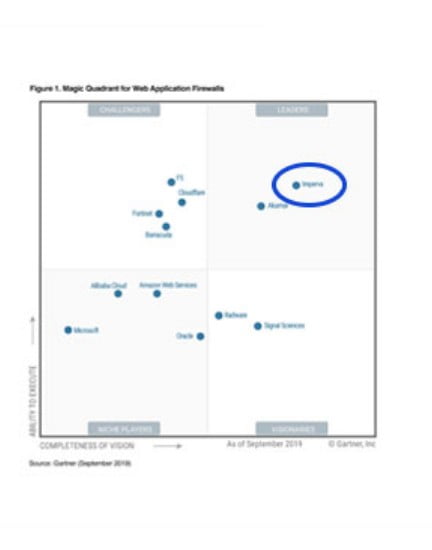 waf
waf





















