ISMS-P Certifcation Consulting
ISMS-P, an information protection and privacy certification consulting system, provides certification for the suitability of information protection and privacy management systems to protect key information assets from various internal and external threats.
It is a certification that integrates the information protection management system (ISMS) under the jurisdiction of the Ministry of Science and Technology and ICT, and the personal information management
system under the jurisdiction of the Korea Communications Commission and the Ministry of Public Administration and Security. In order to establish an appropriate information protection system for an organization, the Korea Internet & Security Agency (KISA) evaluates the system objectively and independently and certifies the compliance of various information protection measures.
It is a certification that integrates the information protection management system (ISMS) under the jurisdiction of the Ministry of Science and Technology and ICT, and the personal information management
system under the jurisdiction of the Korea Communications Commission and the Ministry of Public Administration and Security. In order to establish an appropriate information protection system for an organization, the Korea Internet & Security Agency (KISA) evaluates the system objectively and independently and certifies the compliance of various information protection measures.
Certification of information protection management system
According to Article 47 (1) of the Information and Communication Network Act, the Minister
of Science and ICT may certify whether the information protection management system,
including administrative, technical, and physical protection measures, meets the standard
Information protection management system certification target
- A Provider of information and communication network services
- A Integrated information and communication facility operator
- A Business operator whose annual sales, revenue, etc. are more than 150 billion won, or whose previous year's sales are more than 10 billion won, or whose average daily number of users is more than 1 million for three months
Features
- Establish an information protection system suitable for your organization's competence and work environment
- Organize 'ISMS deployment TFT' to help organizations adapt to information protection management systems quickly to perform knowledge transfer
- Meet the requirements of the information protection management system along with the production of outputs that meet the certification review criteria

Action and response to information system vulnerabilities
Strengthening the ability to respond to infringement accidents
Establishment of information protection and personal information system
Securing legal compliance
Obtaining ISMS-P Certification
Improve information protection management
Goals
Establish, document, and continuously manage procedures and processes to improve the stability and reliability of an organization's assets
Supports a set of processes and activities to realize confidentiality, integrity, and availability of information that is an information protection objective
Provide management, physical, and technological responses through the establishment of an information protection management system
Consulting methods
Based on BOSSᶜᵐ, a methodology for establishing an information protection management system, modules suitable for each task are combined to proceed in the order of initiation, vulnerability diagnosis, risk analysis, countermeasure establishment, and termination.
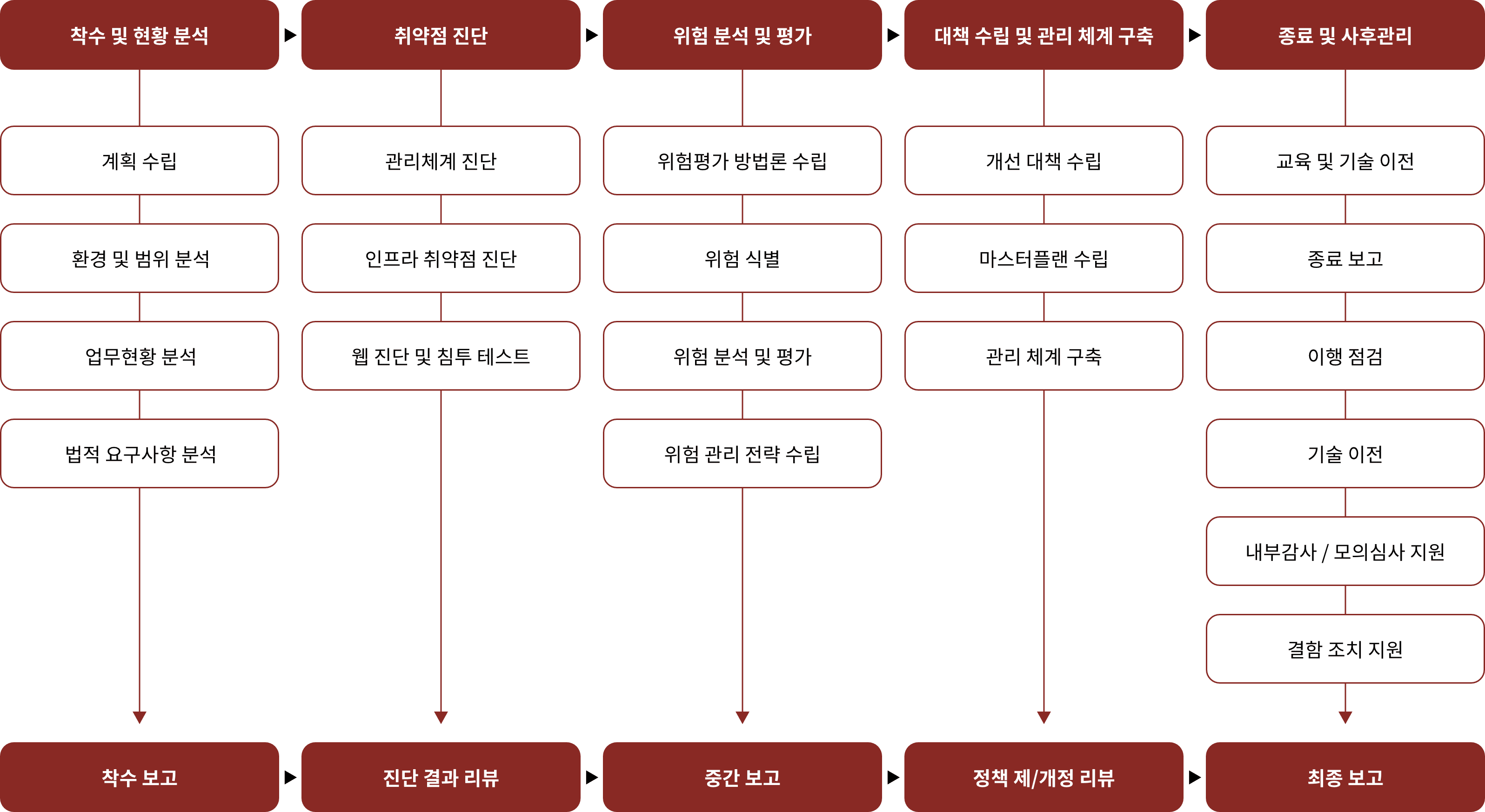
 Understand current status and assets
Understand current status and assets
Understand current status and assets
In order to analyze the current status of security, information assets are closely identified,
security ratings/importance calculations, and information assets held are identified to determine
the scope and target of vulnerability diagnosis.
 Management/physical checks
Management/physical checks
Management/physical checks
It consists of 12 controls in the 5th stage of information protection management process,
92 controls in 13 areas of information protection measures, and 104 controls. It is the standard of the
objective information protection management system, so the level of information protection and management system are diagnosed.
 Technical vulnerability diagnosis
Technical vulnerability diagnosisand simulated hacking
Technical vulnerability diagnosis
and simulated hacking
and simulated hacking
The calculated information protection system is diagnosed with technical vulnerabilities
and simulated hacking to derive weaknesses in the institution's major
information systems and to provide countermeasures.
 Risk assessment and protection measures
Risk assessment and protection measures
Risk assessment and protection measures
Create and catalog asset details, assess asset confidentiality, integrity,
and availability to assess asset importance, specify acceptance risk levels,
risk acceptance and countermeasures based on vulnerability analysis, and create
protection measures based on specified risk analysis results.
Expectation Effectiveness
Qualitative Effect
- Improve corporate credibility and market competitiveness through the establishment of a comprehensive information protection system
- Respond more effectively to the latest trends in security incidents: intelligent attacks
- Improving the level of information security by improving the information security management system
Quantitative Effect
- Compliance with the Information and Communication Network Act
- Mitigate legal responsibility in the event of a security incident
- Gain confidence from customers and partners who are sensitive to information protection, resulting in higher sales
